Copyright 2007-25 Digital Media Law Project and respective authors. Except where otherwise noted,
content on this site is licensed under a Creative Commons Attribution-Noncommercial-ShareAlike 3.0 License: Details.
Use of this site is pursuant to our Terms of Use and Privacy Notice.
content on this site is licensed under a Creative Commons Attribution-Noncommercial-ShareAlike 3.0 License: Details.
Use of this site is pursuant to our Terms of Use and Privacy Notice.




 As a Los Angeles Superior Court prepares to break new ground concerning defamation on
As a Los Angeles Superior Court prepares to break new ground concerning defamation on  Whether we consider the
Whether we consider the 
 In the days of unwarranted government surveillance and elaborate data collection, people increasingly rely on anonymizing services to keep their online activities private, such as proxy servers, encrypted cloud storage, and virtual private networks. Virtual private networks, or VPNs, route online communications through a secure and encrypted private network to a remote server (sometimes in a jurisdiction with greater protection for freedom of speech or weaker law enforcement).
In the days of unwarranted government surveillance and elaborate data collection, people increasingly rely on anonymizing services to keep their online activities private, such as proxy servers, encrypted cloud storage, and virtual private networks. Virtual private networks, or VPNs, route online communications through a secure and encrypted private network to a remote server (sometimes in a jurisdiction with greater protection for freedom of speech or weaker law enforcement). In December 2011, hacktivist collective Anonymous (in)famously
In December 2011, hacktivist collective Anonymous (in)famously  On June 25, 2013, the Opinion of the Advocate General Niilo Jääskinen (AG) in case C-131/12,
On June 25, 2013, the Opinion of the Advocate General Niilo Jääskinen (AG) in case C-131/12, 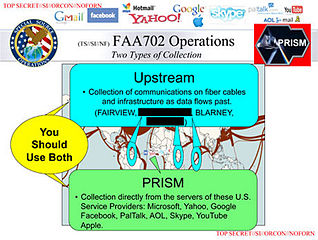 (This is the second part of a two-part post. In
(This is the second part of a two-part post. In 
Description:
The defendant, Hunter Moore, founded a now-defunct website at the URL IsAnyoneUp.com, which hosted sexually explicit user-submitted photos and videos. The plaintiff, James McGibney, owns a website called BullyVille, which works to counsel people who have been bullied by offering advice from professionals. McGibney bought the domain name for IsAnyoneUp.com from Moore on April 19, 2012. After the purchase, Moore referenced McGibney in tweets sent from his twitter handles @huntermoore and @is_anyone_up.
On August 20, 2012, McGibney filed a complaint against Moore in the District Court of Clark County, Nevada for defamation per se and false light. McGibney's complaint denied assertions made in Moore's tweets. McGibney claimed that Moore's tweets suggested that McGibney was a pedophile, a child abuser, and that McGibney possessed illegal content obtained from IsAnyoneUp.com. (Moore's full tweets can be viewed as exhibits to the complaint.)
On the defamation claim, the complaint alleged that Moore posted the statements intentionally, with the specific malicious intent to harm McGibney's reputation, and with actual malice, as Moore knew the statements were false at the time he tweeted them or else had reckless disregard for the truth. The complaint asserted damages relating to McGibney's business, as Moore's tweets referenced McGibney's connection to BullyVille.
On the false light claim, the complaint stated that Moore portrayed McGibney as a pedophile and child abuser on Moore's twitter account. The complaint said Moore's statements were categorically false, made with actual malice, and highly offensive to any reasonable person. It alleged that, by publishing the "false and harmful statements" to a Twitter following of over 160,000 people, Moore gave publicity to such statements.
The complaint requested: (1) more than $10,000 on the defamation claim for harm to McGibney's reputation; (2) more than $10,000 on the false light claim for resulting mental harm; (3) more than $10,000 for Moore's willful, deliberate, and malicious defamation of McGibney; (4) attorney's fees and related costs; and (5) any additional relief ordered by the Court.
On February 26, 2013, the plaintiff filed affidavits for Colleen Connolly-Ahern and Steven Rohr in support of an application for a default judgment against Moore. Connolly-Ahern, an Associate Professor of Advertising and Public Relations at the Pennsylvania State University, evaluated the McGibney's defamation claim against Moore. Her affidavit stated that because of Moore's "quasi-celebrity status" he will have a "larger-than-normal percentage" of followers who believe his statements about McGibney are truthful. Rohr, a founder and president of a Public Relations organization, confirmed the statements made in Connolly-Ahern's affidavit and added that with the existence of sites like www.archive.org, an Internet Archive, Moore's allegations may follow McGibney for years to come and damage his professional reputation. Rohr also stated that Moore's tweets caused real and tangible "lifetime reputational harm" to McGibney, which justified a judgment of $250,000.
The next day, on February 27, 2013, the plaintiff filed an affidavit of J. Malcolm DeVoy, one of the plaintiff's attorneys. DeVoy's affidavit included a copy of McGibney's redacted billings totaling $8,003.00.
On March 8, 2013, the court entered a default judgment against Moore for defamation and false light. The court held that Moore falsely accused McGibney of serious crimes and offenses that were defamatory per se. The court stated that Moore had been properly served with process and Moore had acknowledged the service on his tweets. The court referenced the affidavits of both Connolly-Ahern and Rohr and specifically addressed Rohr's mention of a $250,000 judgment, stating that the affidavits and Rohr's oral testimony were sufficient to support a judgment of $250,000 against Moore. Accordingly, the court ordered that Moore pay: (1) $250,000 in damages; (2) Interest accruing at 3.25%/month until the judgment is paid in full; (3) $1,588.50 for suit costs; and (4) $11,581.00 in attorney's fees.
On March 12, 2013, a notice of entry of default judgment was filed and on April 19, 2013, a writ of execution was issued to the Constable of Clark County, Nevada for $263,169.50 against Moore, commanding that the judgment be satisfied via Moore's Bank of America checking, savings, or other financial account.