 (This is the second part of a two-part post. In Part One, Bryce Newell examined the implications of government collection and analysis of metadata relating to electronic communications. Today, Bryce picks up from where he left off, considering the implications of government surveillance under different conceptions of freedom.)
(This is the second part of a two-part post. In Part One, Bryce Newell examined the implications of government collection and analysis of metadata relating to electronic communications. Today, Bryce picks up from where he left off, considering the implications of government surveillance under different conceptions of freedom.)
The International Covenant on Civil and Political Rights (ICCPR), a widely ratified international human rights treaty, includes provisions that relate to liberal and republican conceptions of freedom that are relevant to current discussions about mass government surveillance and communications intelligence gathering. Article 17 of the ICCPR states that, “No one shall be subjected to arbitrary or unlawful interference with his privacy, family, home or correspondence, nor to unlawful attacks on his honour and reputation.” Article 18 guarantees the freedoms of thought, conscience, and religion, and Article 19 guarantees the “right to hold opinions without interference” and the “right to freedom of expression.” The European Convention on Human Rights, an important regional – rather than truly international – treaty, also provides similar protections, as do the constitutions and charters of many other democratic countries. The relevance of these treaties and philosophical accounts of freedom are tied directly to all three of the questions posed in my first post in this series but, I think, they are most interesting when applied to the third question: what transparency and oversight mechanisms ought to govern the collection of communications information by governmental intelligence agencies?
As a starting point, we should seek to identify the oversight mechanisms that are currently in place. In the United States, much of this recently discussed surveillance takes place under the auspices of the Foreign intelligence Surveillance Act (FISA), as amended by the U.S. PATRIOT Act of 2001 and FISA Amendments Act of 2008 (among others). In Canada, the Communications Security Establishment (CSEC) relies on the interconnected provisions of a number of laws, such as the National Defence Act (NDA), the Criminal Code, the Privacy Act, and the Canadian Charter, as well as a number of classified Ministerial Directives (MDs) and Ministerial Authorizations (MAs) that authorize specific activities, including the incidental collection of information about domestic persons. In the United Kingdom, the activities of the Government Communications Headquarters (GCHQ) are regulated by the Regulatory Investigatory Power Act. All of these agencies are restricted in various ways from targeting domestic persons, and their respective security and human intelligence-oriented agency partners (e.g. the CIA and FBI in the U.S., CSIS in Canada, and MI-5 and MI-6 in the UK) and law enforcement agencies are also somewhat restricted in their abilities to collect information about domestic persons without appropriate grounds to do so (e.g. some form of warrant, administrative subpoena, or ministerial authorization).
However, as made clear in recent public congressional hearings and court cases in the United States, much of the legal basis for individual surveillance programs (e.g. the classified decisions of the Foreign Intelligence Surveillance Court (FISC)) remain undisclosed. Federal agencies claim multiple layers of oversight by other agencies (the FISC, Justice Department, and attorney’s in multiple offices), and Congress does get private briefings from intelligence chiefs that are not made public. Canadian intelligence agencies are also subject to oversight by ministers and, in terms of CSEC, to an appointed and independent Commissioner. British intelligence is likewise subject to oversight. The problem, from the point of view of the ordinary people, is not necessarily with the existence of the surveillance programs themselves; rather, it is largely with the lack of transparency and openness (perhaps combined with a certain level of distrust in government officials who have authorized these programs for a number of years).
In one recent U.S. case, Clapper v. Amnesty International, the Supreme Court held that a number of human rights and other organizations could not challenge the constitutionality of the provisions of FISA, which authorizes the government to intercept communications between U.S. citizens and foreign nationals (or those suspected of being foreign nationals), and to maintain secrecy about whose correspondence the government has intercepted. The organizations claimed that, because of their regular communications with overseas persons, there was an “objectively reasonable likelihood that their communications will be acquired… at some point in the future” and that the threat of this acquisition had caused them to take costly preventative measures aimed at preserving the confidentiality of their communications. Despite the fact that, due to the law’s secrecy requirements, the government is the only entity that knows which communications have been intercepted, the Supreme Court held that third-parties like Amnesty International do not have standing to challenge the Act because they cannot show that they have been harmed (precisely because they don’t have access to information about the government’s surveillance activities).
The government has defended its secrecy in a number of prior and ongoing cases (see here, here, here, here, and here for a few examples). And while some secrecy is undoubtedly necessary (as even the ACLU admits) to properly enable these agencies to prevent attacks on domestic and international soil, the current discussions about the extent of that secrecy is important and severely needed. Currently, we don’t know much about what electronic surveillance activities governments are engaged in, what types of information they are collecting as part of these activities, what use this information is being put to, and the FISA Court’s interpretations of the legal basis for each of the programs. The recent disclosures, and others in the past, have shed some light on these issues, but they are far from comprehensive.
In cases challenging secret surveillance in Europe, the European Court of Human Rights (ECtHR) has stated, in terms that resonate with both the civic-republican notion of freedom as the lack of susceptibility to arbitrary domination and the more liberal idea of freedom as noninterference, that:
[T]he mere existence of legislation which allows a system for the secret monitoring of communications entails a threat of surveillance for all those to whom the legislation may be applied. This threat necessarily strikes at freedom of communication between users of the telecommunications services and thereby amounts in itself to an interference with the exercise of the applicants’ rights… irrespective of any measures actually taken against them. [Case of Liberty and Others v. The United Kingdom, ¶ 56]
According to Neil Richards, an American law professor,
The bottom line about surveillance and persuasion is that surveillance gives the watcher information about the watched. That information gives the watcher increased power over the watched that can be used to persuade, influence, or otherwise control them, even if they do not know they are being watched or persuaded. [link to PDF at Harvard Law Review]
These ideas, in concert with the requirement in the ICCPR that “No one shall be subjected to arbitrary or unlawful interference with his privacy, family, home or correspondence,” demonstrate the need for substantive discussion about government surveillance and effective oversight by governmental bodies, elected officials, news media, and the public themselves. This may require the declassification of certain documents, including legal interpretations of laws authorizing surveillance activities, and a greater level of transparency (such as proposed by the Ending Secret Law Act). Either way, secretive government surveillance may actually interfere with our rights to intellectual or informational privacy – the rights to access, acquire, and use information, and to control information about ourselves. It might also infringe on our rights to free expression and chill speech, including both speech itself and searching for information as a predicate to speaking. If, however, we cannot access knowledge about whether we have, in fact, been interfered with (including high-level information about general government practices), then approaching the question from a position informed by civic-republican concerns about limiting arbitrary domination becomes highly relevant and important. As presented above, “the mere existence of legislation which allows a system for the secret monitoring of communications entails a threat of surveillance” and, if that power is exercised in an arbitrary fashion, has serious implications for our freedoms, regardless of whether we have actually been sucked into the NSA data vacuum.
On the other hand, increased transparency may also have some negative impact on the efficiency and effectiveness of counter-terrorism efforts. These interests are not insubstantial. As a result, transparency measures should be tailored to respect legitimate national security interests. Ultimately, however, some additional transparency – and some reduction in potential domination – might be justified precisely because it increases the political freedoms of the people. We might claim greater democratic interest in information about secret legal interpretations or methods used to conduct surveillance than about the substantive information actually collected – but we might draw lines in different places as well. Actual interference needs to be adequately justified, and the potential for arbitrary domination by governments must be severely limited. How best to address these concerns is a pressing question. Regardless of where we ultimately end up, answering and debating these questions will have important ramifications for how we think about our political freedom – and how much freedom we ought to let slip away for the sake of security.
Bryce Clayton Newell is currently a Google Policy Fellow at the Samuelson-Glushko Canadian Internet Policy and Public Interest Clinic (CIPPIC) at the University of Ottawa Faculty of Law in Ottawa, Ontario. He is also a doctoral student in Information Science at the University of Washington in Seattle, Washington, a licensed attorney (California, inactive) and a documentary filmmaker. The opinions expressed in this post are those of the author alone, and not of any of the organizations to which he is affiliated. The author thanks CIPPIC for allowing him to pursue this line of research as part of his related work at the Clinic. Bryce can be reached at bcnewell@uw.edu.
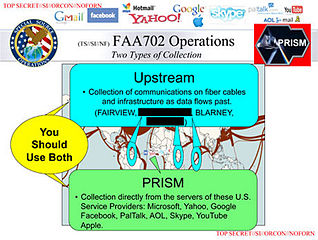
(Image: NSA slide leaked by Edward Snowden describing the PRISM surveillance program)